Simple Locker from Not So Boring Android Malware
This is a sample gathered from Not So Boring Android Malware.
Surface Analysis
Let’s start this analysis by opening the sample apk file on an Hex Editor.

We can already identify some highly suspicious strings.
We can also open the apk on the Jadx-gui to verify.

Static Analysis
By taking a quick look at the AndroidManifest.xml file, we can observe that the app only has 1 activity, 1 service and 1 receiver.
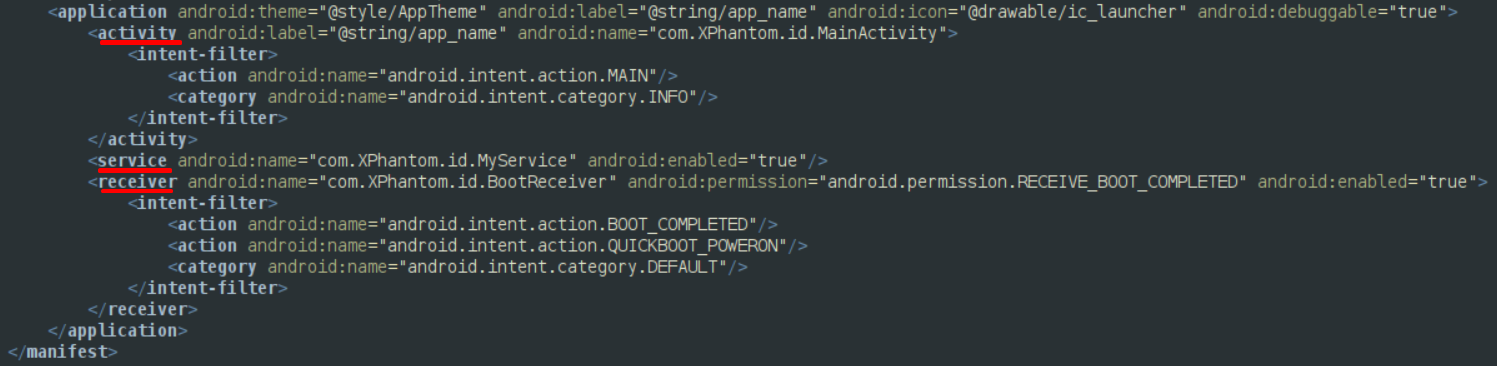
The activity MainActivity starts the service, MyService, as it is created.
The receiver,BootReceiver, listens to 2 kinds of actions, BOOT_COMPLETED and QUICKBOOT_POWERON. This is a form of persistence, as the malware will restart every time the device reboots (or cold boots).
On the OnReceive method of this receiver, it also sends an intent to start MyService.
This indicates that the main behavior of this app is done on the service, MyService.
Locking Functionality
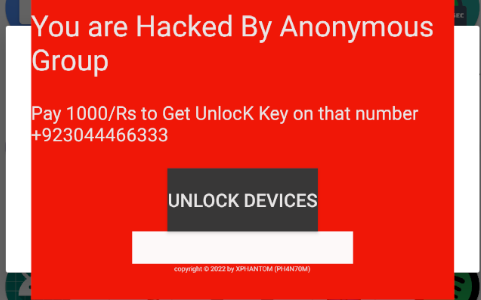
This is the layout presented to the user when it launches the app by clicking on the icon or by rebooting the device. The user is prevented from clicking away from this interface.
This is done on MyService by inflating this layout (main.xml) to a view with the layout parameters defined here:
new WindowManager.LayoutParams(-2, -2, 2002, 1, -3);
The 2002 value refers to the window type: TYPE_PHONE. According to the Documentation, these windows are placed above all applications, but behind the status bar.
This application falls under the category of ransomware, as it demands a ransom to “unlock” the device. However, if we analyze the code triggered when the button is clicked, we can state some interesting facts:
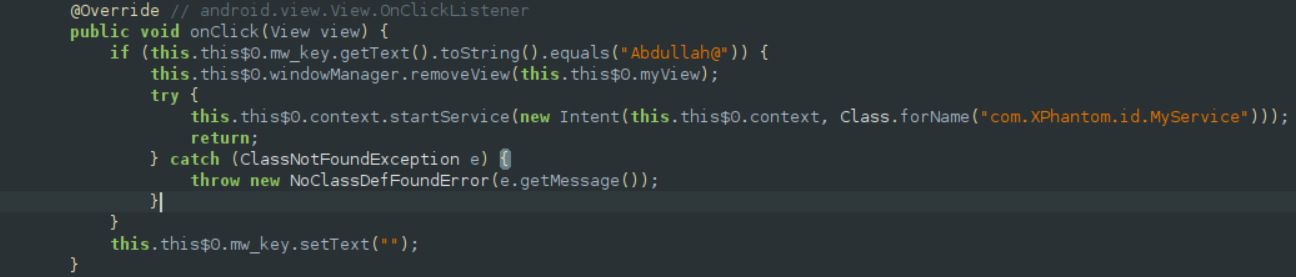
1 - If the user inserts the supposed “key” (Abdullah@) to unlock the device, the service will be started once again.
2 - If the user inserts an “incorret key”, nothing changes.
Conclusion
In summary, there’s no real unlocking of the device, unless the user uninstalls the app through adb or it just stops working, as it happened during the dynamic analysis on the emulator. This sample was a really simple one, being the first one from the Easy Samples section on Not So Boring Android Malware.
IoCs
APK SHA256 hash: 5251a356421340a45c8dc6d431ef8a8cbca4078a0305a87f4fbd552e9fc0793e
